ECMath project MI11: "Data mobility in ad-hoc networks: Vulnerability and security"
Project heads
Prof. Dr. Wolfgang König and Dr. Benedikt Jahnel
Staff
Alexander Hinsen (ne Wapenhans)
Internal Collaboration
External Cooperation
Dr. Christian Hirsch Aalborg University, Aalborg Denmark and Orange Research Labs, Paris France
This research is carried out in the framework of Matheon supported by Einstein Foundation Berlin


Project background
Present day telecommunication networks are ill equipped for the rapidly growing demand for mobile data transfers. With the fifth generation of mobile networks, paradigmatic shifts in the design of the network are on the agenda. A critical aspect here is the role of infrastructure. Multilayered cellular networks with possible incorporation of relaying mechanisms are under investigation not only in the scientific community [Baceelli et al. 2009, Dousse et al. 06], but also in industry [3GPP 2010]. All these new designs have in common a rapid increase of degrees of freedom in the system. The central role of (expensive) base stations is reduced in favour of an increasingly important role of (cheap) relays. In particular, also the users of the system will be attached a relay functionality in the system. As a result, the network becomes more and more decentralised. First implementations of peer-to-peer (P2P) communications for public use are already available see for example the application Firechat. Exploring the possible benefits of such new architectures is in full swing in the academic and the industrial research.
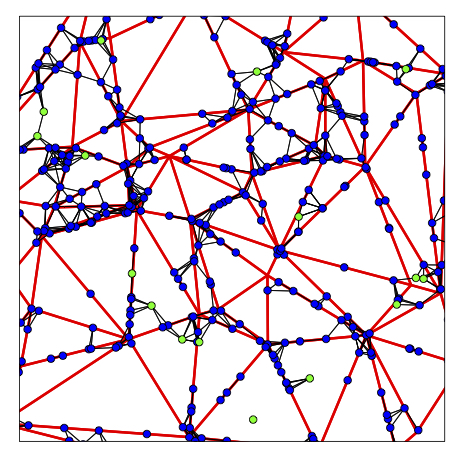
One promising way to cope with the new and more complex structures that arise is to exploit probabilistic methods. Indeed, fundamental ansatzes from stochastic geometry (e.g., spatial Poisson processes, continuum percolation theory, ...) are widely used for modelling the spatial locations of the users, the relays and the base stations and their basic connectivity properties. For the description of temporal developments, standard methods from stochastic processes (stochastic interacting particle processes like bootstrap percolation or the contact process) are commonly used to model the spread of information through a network, see e.g., [Chatterjee and Durrett 2010].
Of crucial importance in all these future scenarios with less centralised architectures is a good understanding of vulnerability and security, in particular of the way in which malware (e.g., proximity-based propagation sabotage software or computer killing viruses like Cabir or CommWarrior) spreads in such networks. For usual networks, a number of strategies have been exploited by operators in order to restrict the spread of the malware and to keep the functionality of the network available. However, the new challenges accompanying the system decentralisation also include the question how successful these defense strategies can be in such systems, in particular since the spread of malware (more generally, of any information) in such a system follows a different set of rules than in centralised networks.
This is the question in which we want to make progress: the proposed project aims at a probabilistic analysis of (1) the velocity of the propagation of infected or otherwise flawed relays if a malware has attacked some node(s), and (2) of the performance and the success of some of the most widely used security strategies against this. We strive to understand how quickly the region of damaged nodes spreads out, in particular whether, under the defense strategies that we consider, the infected region will be kept bounded or not. We will also aim at developing new variants of defense strategies that are adapted to the new challenges of the less centralised architecture.
An important feature of this proposal is that our results will be derived in a particularly realistic setting, as we will not only embed the network in the two-dimensional euclidean space (as is done in many research papers), but even in some random street models (embedded in the euclidean space). Additionally we will assume that the users of the telecommunication system are (randomly) placed on these street systems.
Aims of the project
We aim for a detailed probabilistic analysis of the propagation of a malware that is initially placed at possibly several (random) nodes in the system. In the first scenario the network is not equipped with any defense mechanism and malware can distribute according to an adequate choice of propagation rules. In the second scenario defense strategies are available and their contribution will be investigated. The goal is to evaluate and compare the efficiencies of some of the main such strategies. This analysis will be carried out in a spatially randomly distributed systems of users and additional relays, and the time evolution of the infection will be the main object of study. The users will be randomly placed on a street system, embedded in the euclidean space. The main results are going to be derived using both, theoretical analysis (on mathematical models for random streets) and computer simulations (using the above mentioned statistical tool provided by Orange). The two findings will be tested against each other.
Project-related WIAS-publications
DOI: 10.20347/WIAS.PREPRINT.2392
DOI: 10.20347/WIAS.PREPRINT.2466
DOI: 10.20347/WIAS.PREPRINT.2479
DOI: 10.30757/ALEA.v15-24
DOI: 10.1007/s11134-017-9555-9
DOI: 10.1017/apr.2016.65
DOI: 10.1017/apr.2017.35
DOI: 10.20347/WIAS.PREPRINT.2463
DOI: 10.20347/WIAS.PREPRINT.2479
DOI: 10.20347/WIAS.PREPRINT.2469
Project-related literature
DOI: ETSI TS 136 300 V9.4.0
DOI: 10.1561/1300000006
DOI: 10.1214/09-AOP471
DOI: 10.1017/S0021900200001820